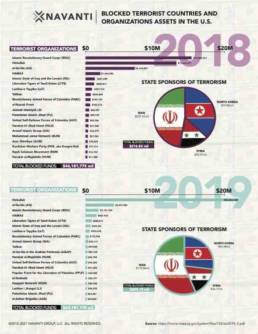
Contracts
Contracts
Navanti Group has been awarded several key contracts by the General Services Administration (GSA), establishing its presence across various government initiatives. Among these is a multi-year Multiple Award Schedule (MAS), Indefinite Delivery, Indefinite Quantity (IDIQ) contract, enabling Navanti to offer its services across government-wide contracts for commercial supplies, services, and solutions. The MAS contract streamlines the procurement process, connecting government buyers with private sector solutions at fair and reasonable prices.
Additionally, Navanti has secured seats on multiple IDIQ contracts such as the Management Excellence for Operations (MEO), Analytical Services IV (ASIV), and the Governance Integration for Stabilization and Resilience in the Middle East and North Africa (GISR MENA) Consortium. These contracts allow Navanti to provide vital support to U.S. government agencies, including USAID, in strengthening operational performance, supporting democracy and governance initiatives, and enhancing stability and resilience in conflict-affected regions. Through these contracts, Navanti offers technical assistance, performance data analysis, program design, and rapid response capabilities to address evolving challenges in governance and development across the globe.
Navanti’s success extends into defense, with a multi-year contract from the U.S. Air Force to conduct Global Market Research Reports (GMRR). This contract focuses on enhancing industrial preparedness by analyzing global logistics networks and supply chain issues across 59 nations. Additionally, Navanti is part of OASIS Small Business (SB), a government-wide IDIQ contract providing flexible, innovative solutions for complex professional services. This positions Navanti as a trusted partner for program management, engineering, financial, and logistical services across a wide range of mission areas.
Join the Team
Join the Team
Navanti recruits multi-talented people, who possess a curiosity about the world and a desire to make a positive difference. We celebrate diversity and promote multi-disciplined approaches. At Navanti, recruits join high-performance teams, enjoy unique career developing opportunities, and work on solving some of the most challenging problems of our time.
Interested in applying for a position, but don’t see one that fits right now?
Send your resume for future consideration to careers@navantigroup.com
CURRENT OPENINGS
Do really interesting work
Help to solve some of the world’s most challenging problems from international development, public health, security, and risk management.
Have a voice
We eschew traditional hierarchies because they stunt potential. We believe everyone has unique value to add regardless of age or title. We celebrate great ideas that can help our clients meet their objectives, and so we have institutionalized the practice of idea-sharing and development at all levels.
We honor drive and excellence
Our meritocratic system provides great rewards to those who excel and drive the business.
Be creative
We encourage fresh thinking because that’s what drives innovation in our field.
Partners: Central Asia Barometer
Partnership with Central Asia Barometer

Central Asia Barometer (CAB) and the Navanti Group (Navanti) have signed a partnership agreement to underpin a long-term cooperation program. Given the strong mutual interest in international research cooperation, CAB and Navanti recognize the benefits derived from further establishing collaboration, cooperation, and interaction with one another. The Parties intend to strengthen this partnership through joint social science research, dissemination of results, and other relevant areas.
About: Central Asia Barometer (CAB) is a regional, independent, non-profit institution for applied social research and analytics on topics of public interest. CAB measures the social, economic, and political “atmosphere” in the countries of Central Asia. The results of CAB’s research help partners like Navanti to make data-based decisions in the best interests of the region’s citizens. CAB conducts regular applied social science research studies and analytically reflect on social processes. In this way, CAB contributes to in-depth, democratic institutional developments in these countries.
Quantitative Data Collection
Quantitative Data Collection
Navanti has created representative samples for the quantitative surveys it conducts in fragile and conflict-affected areas since 2015. We employ our own trained field research teams in conjunction with local and third-party datasets and emergent geospatial technologies for subsequent data collection. Representative sampling is often a challenge due to missing or outdated data, population displacement, fluid conditions, and issues of access. While Navanti begins with census data or official population projections wherever possible, these are often insufficient, particularly in conflict zones and when sampling is needed at district or other local levels. Within northeastern Nigeria, Yemen, Tajikistan, Kyrgyzstan, southwestern Niger, and northern Burkina Faso, Navanti has employed field researchers to consult with local leaders and other key informants on the ground for current data on displacement, population distribution and access, and has used geofencing to map localized areas including formal and informal IDP settlements, informal neighborhood boundaries, and rural hamlets. This data is then triangulated with satellite imagery, gridded population density estimates, and displacement tracking datasets to create sample frames for multistage clustering using population proportional to size (PPS).
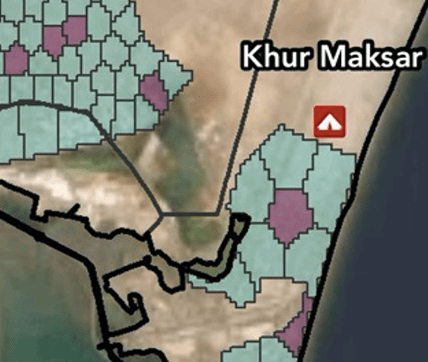
As with Navanti’s other approaches to field data collection, we adhere to best practices in ensuring that survey data collection:
- does no harm; upholds safety and comfort of participants
- enumerators, and others associated with fieldwork
- remains conflict- and gender-sensitive from design through execution
Survey instruments are regularly scoped and designed in collaboration with our clients and our field teams together, to:
- adapt needed data points and established scales to local contexts
- identify key vulnerable populations and set appropriate procedures for their inclusion
- introduce data collection to community stakeholders
- adapt results of pre-testing and piloting. Instruments are regularly translated and back-translated into relevant local languages, including discussion of sensitive and localized terms with field teams.
Remote and hybrid approaches to training, capacity building, management, and quality control are not new to Navanti. Since our founding, we have used emerging information technologies to prepare teams for the field and ensure data quality in numerous challenging environments, and quite often in locations with low or minimal digital connectivity. We have learned to adapt our training, field supervision, and quality control practices to whatever the conditions allow, from live video feed connecting stakeholders across the globe, to asynchronous learning and discussion with intermittent touchpoints. Above all, we work to develop the capacities of our colleagues in the field and develop reliable partnerships to adhere to the highest data collection standards.
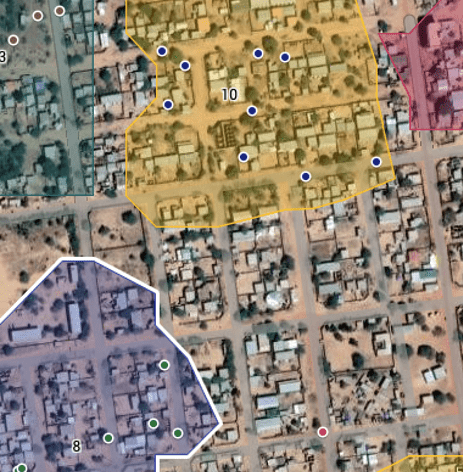
Understanding the need for trust and rapport between enumerators and participants in the brief interaction for data collection, Navanti has always sought to select enumerators from among members of communities chosen for data collection, so that they may be met by participating households and individuals as neighbors rather than outsiders. Just as definitions and meanings of community vary widely, enumerator selection applies considerations of gender, age, sexual orientation and gender identity and expression (SOGIE), ethnicity, and other markers of identity and belonging as appropriate to each study and its context. For survey data collection, gender is perhaps among the most important markers of identity, and Navanti understands that both gender-sensitivity and data quality requires same gender data collection (women interviewing women, and men interviewing men) in many cases depending on context and research topic. We approach every quantitative data collection effort as an opportunity to learn together with our colleagues in the field and improve our application of gender standards to the particular contexts of communities where we work – through our training, field supervision, quality assurance, and analysis.
Change Management at Navanti
Change Management at Navanti
Change Management at Navanti
Navanti personnel take an assets-driven approach to change management. Our client assessment begins with an indication of the resources, needs, and tolerance for change implementation. Sample components are strategy development, implementation plans, data collection, measurements of change effectiveness, and stakeholder communication plans.
Navanti has used different change management approaches depending on client needs including the Capacity, Opportunity, Motivation-Behavior (COM-B) Model and its associated Behavior Change Wheel and Navanti’s own Purpose, Process, People Model (3Ps).

Recent examples include:
USAID Mission Management Assessment (MMA) Change Management that supported the Bureau of Management’s Performance Division to develop a plan to manage change for the revitalized policy guidance and implementation process for Operating Units undertaking MMAs. Specifically, Navanti developed a change management plan, surveys of stakeholders on the MMA process and recommendation implementation, a rebranding strategy, and assessments to evaluate the ease, efficiency, and effectiveness of the updated policy and guidance. Furthermore, Navanti supported USAID with a communications strategy to initiate an Agency-wide perception change.
UNDP Change Management that supported a country-level assessment of sustainable best practices in North Macedonia. The research revolved around municipalities, local institutional capacities and legal requirements surrounding stray dog population response measures in six municipalities. We provided actionable recommendations and models for population management and transitional shelter establishment and management.
Monitoring, Evaluation, and Learning
Monitoring, Evaluation, and Learning
Navanti is currently the implementer for the USAID/Nigeria MEL Support Activity, providing assistance related to field-based monitoring, evaluations, knowledge management, and collaborating, learning, and adapting (CLA).
Monitoring
Navanti has a long history of conducting Third Party Monitoring (TPM) for a range of development and governmental actors across Europe, Africa, the Middle East, and Asia. In non-permissive environments, Navanti’s researchers can access places safely and ethically to assess the conditions or progress toward a development project outcome. Even when the context is more stable, Navanti can be an independent, unbiased verifier of progress made and the context as it exists in a way that development actors and especially those managing the programs may not be able to. Finally, while program managers strive to do as many site visits as possible, Navanti can magnify the ability of its clients to monitor a much large set of activities given its extensive networks.
Countries in which Navanti has conducted monitoring: Syria, Yemen, Nigeria, Somalia, Kosovo, Iraq, Mali, Mozambique
Evaluation
Navanti also has extensive experience in conducting evaluations for a range of international partners. Evaluations can serve a range of purposes depending on when they occur. Generally the goal is to learn about whether an intervention was effective and how and why/why not to apply to the existing intervention if the evaluation is done in during the implementation or for future interventions and the broader community of practice when conducted at the end. There are many approaches to evaluation, and which are most appropriate often depends on a range of factors including the nature and scale of the intervention and how sites were chosen, the permissibility of the context, the complexity of the context, amount of funding available for evaluation, and the purpose of the evaluation. While having experience using many different approaches, Navanti specializes in those that are most useful in complex contexts where causality is contested and counterfactuals are unavailable.
Countries in which Navanti has conducted evaluations include: Chad, Niger, Cameroon, Kyrgyzstan, Tajikistan, Nigeria
Learning
Navanti facilitates learning for its clients in various ways. When taken together with monitoring and evaluation, Navanti helps clients learn from the evidence produce and use it to apply to adapting programming and activities. Additionally, Navanti helps clients identify gaps in their knowledge and skills and puts together learning events, whether peer-to-peer learning around a common problem or training in a topic of shared interest for communities of practice. Navanti also helps clients engage in ‘pause and reflect’ exercises both formally and informally to allow for learning and course correction. Other learning work Navanti has conducted includes hybrid remote/in-person training of field teams for focus group discussions, semi-structured key informant interviews, quantitative survey sampling and administration, other data collection instruments and e-learning module development.
Specifically within the USAID context, Navanti helps Missions and their implementing partners use the Collaborating, Learning, and Adapting (CLA) framework to improve effectiveness and produce development outcomes.
Countries in which Navanti has conducted learning-related work: Morocco, Tunisia, Nigeria, Chad, Niger, and Cameroon
Template Page
Partners: Central Asia Barometer 
Central Asia Barometer (CAB) and the Navanti Group (Navanti) have signed a partnership agreement to underpin a long-tetm cooperation program. Given the strong mutual interest in international research cooperation, CAB and Navanti recognize the benefits derived from futher establishing collaboration, cooperation, and interaction with one another. The Parties intend to strengthen this partnership through joint social science research, dissemination of results, and other relevant areas.
About: Central Asia Barometer (CAB) is a regional, independent, non-profit institution for applied social research and analytics on topics of public interest. CAB measures the social, economic, and political “atmosphere” in the countries of Central Asia. The results of CAB’s research help partners like Navanti to make data-based decisions in the best interests of the region’s citizens. CAB conducts regular applied social science research studies and analytically reflect on social processes. In this way, CAB contributes to in-depth, democratic institutional developments in these countries.
Navanti Homepage
Find Topics by Country
Select a country to find categorized news and press related to that nation or region.
Albania
Armenia
Belarus
Bosnia
Cameroon
China
Colombia
Congo
Estonia
Georgia
Greece
Hungary
India
Iran
Iraq
Jordan
Kosovo
Kuwait
Lake Chad
Latvia
Libya
Lithuania
Mali
Moldova
Morocco
Mozambique
Myanmar
Nicaragua
Niger
Nigeria
North Macedonia
Oman
Phillippines
Russia
Saudi Arabia
Somalia
Sudan
Syria
Transnistria
Tunisia
Turkey
Ukraine
Yemen
Our Expertise
Polling & Surveys
Food Security
Risk & Security Analysis
GIS & Mapping
AI & Data Mining

Market Assessments

Crisis, Stabilization and Governance

Staffing & Training
Latest News
Somalia-Egypt Alliance vs. Ethiopia-Somaliland: A Brewing Crisis?
September 6, 2024
Mogadishu Port On January 1, 2024, Somaliland President Muse Bihi Abdi and Ethiopian Prime Minister Abiy…
Spot Report: Hudaydah Port Fuel Storage and Cranes Damaged
July 21, 2024
Merchants have informed Navanti Group that previously operational and refurbished cranes at the Port of…
Three Brothers’ ISIS Attack on Muscat Mosque: Implications for Oman by Mohammed Albasha
July 18, 2024
The Museum of the Frankincense Land in Salalah, Oman Historically, the Royal Oman Police (ROP) have focused…
Where Clients Benefit
For 12 years, Navanti Group’s mission has been to deliver information through on-demand analytical reports, with clients benefiting from subject matter expertise and near real-time data on atmospherics, conflict, and population trends throughout Africa, the Arabian Peninsula, Central Asia, the Levant, and Eastern Europe. Through primary research, publicly available information, and open-source analysis, Navanti’s subject matter experts advise on cultural nuances and answer client driven requests for information in areas of food security, civil society development, peace and conflict, and governance. Each deliverable typically includes imagery, maps, and/or data analysis covering an array of topics including target audiences, local economic conditions, infrastructure, media, humanitarian needs, and socio-cultural assessments.
Why We Are Different
Our Differentiator is that our team has extensive experience managing data collection and understanding cultural norms for difficult environments, including extremely remote locations and conflict zones. Our tenants are Access, Insight, Speed, and Flexibility.
Access – Since 2008, Navanti has built vetted local networks of researchers in over 70 countries throughout Latin America, Africa, Eastern Europe, the Middle East and Central Asia. They are native to the environments in which they operate, providing nuanced access across ethnic group, gender and class lines.
Insight – Access, without a deep understanding of local dynamics is necessary, but not sufficient for acting in emerging markets. Navanti develops and maintains highly trained subject matter experts that combine unparalleled access of our researchers with cutting edge analytical techniques to surface the “why” that that might otherwise go unnoticed.
Speed – Insight, on difficult to acquire in-depth analysis, is useless unless it can be delivered in time to support operational decisions. Navanti structures all data efforts to meet client decision cycles and formats.
Flexibility – Navanti research adapts as local dynamics evolve, providing an opportunistic capacity that enables clients to anticipate and plan for near horizon change. Together, these principles allow Navanti to provide industry best reporting that provides clients with near real-time data.
Navanti Insights
The War in Yemen - The Unbeautiful South
Mohammed Albasha, Communication and Client Engagement Manager at Navanti Group, was interviewed by The Economist on the war in Yemen.
For the first time, an alleged terrorist has broadcast a confession in real time on Facebook Live
John Arterbury, Project Manager at Navanti Group, was cited by Caitlin Dewey and Sarah Parnass of The Washington Post on live-streaming of terror attacks.
Yemen in Focus: Allies turn rivals on strategic Socotra island
Mohammed Albasha, Communication and Client Engagement Manager at Navanti Group, was interviewed by the London-based ‘The New Arab’ on the crisis in Socotra Archipelago.
Quiet Support for Saudis Entangles U.S. in Yemen
Mohammed Albasha, Communication and Client Engagement Manager at Navanti Group, was interviewed by By Mark Mazzetti and Eric Schmitt, The New York Times on the how the quiet support for Saudis entangles U.S. in Yemen.
Privacy Policy
Privacy Policy
Privacy Policy
Last updated: August 16, 2021
This Privacy Policy describes Our policies and procedures on the collection, use and disclosure of Your information when You use the Service and tells You about Your privacy rights and how the law protects You.
We use Your Personal data to provide and improve the Service. By using the Service, You agree to the collection and use of information in accordance with this Privacy Policy. This Privacy Policy has been created with the help of the Privacy Policy Generator.
Interpretation and Definitions
Interpretation
The words of which the initial letter is capitalized have meanings defined under the following conditions. The following definitions shall have the same meaning regardless of whether they appear in singular or in plural.
Definitions
For the purposes of this Privacy Policy:
- Account means a unique account created for You to access our Service or parts of our Service.
- Company (referred to as either “the Company”, “We”, “Us” or “Our” in this Agreement) refers to Navanti Group.
- Cookies are small files that are placed on Your computer, mobile device or any other device by a website, containing the details of Your browsing history on that website among its many uses.
- Country refers to: Virginia, United States
- Device means any device that can access the Service such as a computer, a cellphone or a digital tablet.
- Personal Data is any information that relates to an identified or identifiable individual.
- Service refers to the Website.
- Service Provider means any natural or legal person who processes the data on behalf of the Company. It refers to third-party companies or individuals employed by the Company to facilitate the Service, to provide the Service on behalf of the Company, to perform services related to the Service or to assist the Company in analyzing how the Service is used.
- Usage Data refers to data collected automatically, either generated by the use of the Service or from the Service infrastructure itself (for example, the duration of a page visit).
- Website refers to Navanti Group, accessible from navantigroup.com
- You means the individual accessing or using the Service, or the company, or other legal entity on behalf of which such individual is accessing or using the Service, as applicable.
Collecting and Using Your Personal Data
Types of Data Collected
Personal Data
While using Our Service, We may ask You to provide Us with certain personally identifiable information that can be used to contact or identify You. Personally identifiable information may include, but is not limited to:
- Email address
- Usage Data
Usage Data
Usage Data is collected automatically when using the Service.
Usage Data may include information such as Your Device’s Internet Protocol address (e.g. IP address), browser type, browser version, the pages of our Service that You visit, the time and date of Your visit, the time spent on those pages, unique device identifiers and other diagnostic data.
When You access the Service by or through a mobile device, We may collect certain information automatically, including, but not limited to, the type of mobile device You use, Your mobile device unique ID, the IP address of Your mobile device, Your mobile operating system, the type of mobile Internet browser You use, unique device identifiers and other diagnostic data.
We may also collect information that Your browser sends whenever You visit our Service or when You access the Service by or through a mobile device.
Tracking Technologies and Cookies
We use Cookies and similar tracking technologies to track the activity on Our Service and store certain information. Tracking technologies used are beacons, tags, and scripts to collect and track information and to improve and analyze Our Service. The technologies We use may include:
- Cookies or Browser Cookies. A cookie is a small file placed on Your Device. You can instruct Your browser to refuse all Cookies or to indicate when a Cookie is being sent. However, if You do not accept Cookies, You may not be able to use some parts of our Service. Unless you have adjusted Your browser setting so that it will refuse Cookies, our Service may use Cookies.
- Flash Cookies. Certain features of our Service may use local stored objects (or Flash Cookies) to collect and store information about Your preferences or Your activity on our Service. Flash Cookies are not managed by the same browser settings as those used for Browser Cookies. For more information on how You can delete Flash Cookies, please read “Where can I change the settings for disabling, or deleting local shared objects?” available at https://helpx.adobe.com/flash-player/kb/disable-local-shared-objects-flash.html#main_Where_can_I_change_the_settings_for_disabling__or_deleting_local_shared_objects_
- Web Beacons. Certain sections of our Service and our emails may contain small electronic files known as web beacons (also referred to as clear gifs, pixel tags, and single-pixel gifs) that permit the Company, for example, to count users who have visited those pages or opened an email and for other related website statistics (for example, recording the popularity of a certain section and verifying system and server integrity).
Cookies can be “Persistent” or “Session” Cookies. Persistent Cookies remain on Your personal computer or mobile device when You go offline, while Session Cookies are deleted as soon as You close Your web browser. Learn more about cookies: What Are Cookies?.
We use both Session and Persistent Cookies for the purposes set out below:
- Necessary / Essential Cookies
Type: Session Cookies
Administered by: Us
Purpose: These Cookies are essential to provide You with services available through the Website and to enable You to use some of its features. They help to authenticate users and prevent fraudulent use of user accounts. Without these Cookies, the services that You have asked for cannot be provided, and We only use these Cookies to provide You with those services.
- Cookies Policy / Notice Acceptance Cookies
Type: Persistent Cookies
Administered by: Us
Purpose: These Cookies identify if users have accepted the use of cookies on the Website.
- Functionality Cookies
Type: Persistent Cookies
Administered by: Us
Purpose: These Cookies allow us to remember choices You make when You use the Website, such as remembering your login details or language preference. The purpose of these Cookies is to provide You with a more personal experience and to avoid You having to re-enter your preferences every time You use the Website.
For more information about the cookies we use and your choices regarding cookies, please visit our Cookies Policy or the Cookies section of our Privacy Policy.
Use of Your Personal Data
The Company may use Personal Data for the following purposes:
- To provide and maintain our Service, including to monitor the usage of our Service.
- To manage Your Account: to manage Your registration as a user of the Service. The Personal Data You provide can give You access to different functionalities of the Service that are available to You as a registered user.
- For the performance of a contract: the development, compliance and undertaking of the purchase contract for the products, items or services You have purchased or of any other contract with Us through the Service.
- To contact You: To contact You by email, telephone calls, SMS, or other equivalent forms of electronic communication, such as a mobile application’s push notifications regarding updates or informative communications related to the functionalities, products or contracted services, including the security updates, when necessary or reasonable for their implementation.
- To provide You with news, special offers and general information about other goods, services and events which we offer that are similar to those that you have already purchased or enquired about unless You have opted not to receive such information.
- To manage Your requests: To attend and manage Your requests to Us.
- For business transfers: We may use Your information to evaluate or conduct a merger, divestiture, restructuring, reorganization, dissolution, or other sale or transfer of some or all of Our assets, whether as a going concern or as part of bankruptcy, liquidation, or similar proceeding, in which Personal Data held by Us about our Service users is among the assets transferred.
- For other purposes: We may use Your information for other purposes, such as data analysis, identifying usage trends, determining the effectiveness of our promotional campaigns and to evaluate and improve our Service, products, services, marketing and your experience.
We may share Your personal information in the following situations:
- With Service Providers: We may share Your personal information with Service Providers to monitor and analyze the use of our Service, to contact You.
- For business transfers: We may share or transfer Your personal information in connection with, or during negotiations of, any merger, sale of Company assets, financing, or acquisition of all or a portion of Our business to another company.
- With Affiliates: We may share Your information with Our affiliates, in which case we will require those affiliates to honor this Privacy Policy. Affiliates include Our parent company and any other subsidiaries, joint venture partners or other companies that We control or that are under common control with Us.
- With business partners: We may share Your information with Our business partners to offer You certain products, services or promotions.
- With other users: when You share personal information or otherwise interact in the public areas with other users, such information may be viewed by all users and may be publicly distributed outside.
- With Your consent: We may disclose Your personal information for any other purpose with Your consent.
Retention of Your Personal Data
The Company will retain Your Personal Data only for as long as is necessary for the purposes set out in this Privacy Policy. We will retain and use Your Personal Data to the extent necessary to comply with our legal obligations (for example, if we are required to retain your data to comply with applicable laws), resolve disputes, and enforce our legal agreements and policies.
The Company will also retain Usage Data for internal analysis purposes. Usage Data is generally retained for a shorter period of time, except when this data is used to strengthen the security or to improve the functionality of Our Service, or We are legally obligated to retain this data for longer time periods.
Transfer of Your Personal Data
Your information, including Personal Data, is processed at the Company’s operating offices and in any other places where the parties involved in the processing are located. It means that this information may be transferred to — and maintained on — computers located outside of Your state, province, country or other governmental jurisdiction where the data protection laws may differ than those from Your jurisdiction.
Your consent to this Privacy Policy followed by Your submission of such information represents Your agreement to that transfer.
The Company will take all steps reasonably necessary to ensure that Your data is treated securely and in accordance with this Privacy Policy and no transfer of Your Personal Data will take place to an organization or a country unless there are adequate controls in place including the security of Your data and other personal information.
Disclosure of Your Personal Data
Business Transactions
If the Company is involved in a merger, acquisition or asset sale, Your Personal Data may be transferred. We will provide notice before Your Personal Data is transferred and becomes subject to a different Privacy Policy.
Law enforcement
Under certain circumstances, the Company may be required to disclose Your Personal Data if required to do so by law or in response to valid requests by public authorities (e.g. a court or a government agency).
Other legal requirements
The Company may disclose Your Personal Data in the good faith belief that such action is necessary to:
- Comply with a legal obligation
- Protect and defend the rights or property of the Company
- Prevent or investigate possible wrongdoing in connection with the Service
- Protect the personal safety of Users of the Service or the public
- Protect against legal liability
Security of Your Personal Data
The security of Your Personal Data is important to Us, but remember that no method of transmission over the Internet, or method of electronic storage is 100% secure. While We strive to use commercially acceptable means to protect Your Personal Data, We cannot guarantee its absolute security.
Children’s Privacy
Our Service does not address anyone under the age of 13. We do not knowingly collect personally identifiable information from anyone under the age of 13. If You are a parent or guardian and You are aware that Your child has provided Us with Personal Data, please contact Us. If We become aware that We have collected Personal Data from anyone under the age of 13 without verification of parental consent, We take steps to remove that information from Our servers.
If We need to rely on consent as a legal basis for processing Your information and Your country requires consent from a parent, We may require Your parent’s consent before We collect and use that information.
Links to Other Websites
Our Service may contain links to other websites that are not operated by Us. If You click on a third party link, You will be directed to that third party’s site. We strongly advise You to review the Privacy Policy of every site You visit.
We have no control over and assume no responsibility for the content, privacy policies or practices of any third party sites or services.
Changes to this Privacy Policy
We may update Our Privacy Policy from time to time. We will notify You of any changes by posting the new Privacy Policy on this page.
We will let You know via email and/or a prominent notice on Our Service, prior to the change becoming effective and update the “Last updated” date at the top of this Privacy Policy.
You are advised to review this Privacy Policy periodically for any changes. Changes to this Privacy Policy are effective when they are posted on this page.
Contact Us
If you have any questions about this Privacy Policy, You can contact us:
- By email: info@navantigroup.com